Remote Access Trojans: New Threats Hidden in Image Files
Written on
Chapter 1: The Lazarus Group's Cyber Tactics
North Korean hackers, particularly the infamous Lazarus Group, have been behind numerous high-profile cyberattacks targeting financial institutions and global corporations. Over the years, they have managed to siphon off millions from various cryptocurrency exchanges, orchestrated the WannaCry ransomware attack, and infiltrated Sony Pictures, leading to leaks of unreleased content and sensitive information. Additionally, this group utilizes privacy coins to obscure their financial trails when converting stolen funds into cash.
With a presence spanning more than a decade, this state-sponsored advanced persistent threat (APT) group is among the most sophisticated and prolific in the cyber realm. Driven by deep-rooted political tensions, Lazarus has primarily targeted South Korean organizations, but their cyber onslaughts have also reached the United States and South Africa.
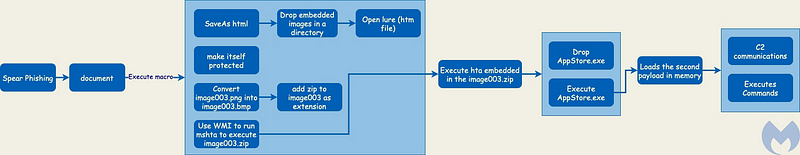
Cybersecurity firm Malwarebytes recently uncovered a novel phishing tactic employed by the Lazarus group. This method involves the use of BMP files that are embedded with malicious HTA objects intended to deploy a Loader. The initial phase of this attack typically involves sending out phishing emails laden with harmful documents. The following illustration outlines the overall attack strategy.
Section 1.1: The Attack Vector
The attack mechanism commences with a phishing Microsoft Office document (???????.doc) that features a lure written in Korean. Victims are instructed to enable macros to view the content, which, when activated, triggers a malicious payload. This payload manifests as a pop-up message claiming to be an outdated version of Office but, in reality, executes an HTA file that has been compressed within a PNG image.
Upon decompression, the PNG transforms into a BMP format, and once initiated, the HTA file deploys a Remote Access Trojan (RAT) disguised as “AppStore.exe” on the compromised system. Security experts have labeled this tactic as a smart way to evade standard security measures since the PNG image hides a compressed ‘zlib’ malicious object, rendering it undetectable by static analysis.
The first video discusses how to investigate malicious disk image files and highlights methods used by cybercriminals to conceal their activities.
Section 1.2: The Functionality of the RAT
Like other Remote Access Trojans, this variant can establish a connection to a command-and-control (C2) server, enabling it to receive commands and execute shellcode. The secondary payload is designed to execute commands and shellcode as well as perform data exfiltration and maintain communication with the command and control server.

Chapter 2: Understanding Steganography in Cyber Threats
The second video explores the use of steganography in malware, particularly focusing on reverse-engineering an XWorm loader that utilizes hidden techniques to evade detection.
Stay informed with the content that matters — Join my mailing list