Best Practices for Cyber Threat Intelligence: A Comprehensive Guide
Written on
Introduction to Cyber Threat Intelligence
A threat refers to any action, whether newly discovered or resurfacing due to past misconfigurations, that could inflict considerable damage on systems. The severity of these threats is often gauged by the resources at risk, as they can result in the theft of sensitive information and compromise data integrity.
For foundational knowledge on threats, please refer to my earlier blog.
While we acknowledge the existence of these dangers, we also understand strategies for mitigating them. Threat analysts gather and analyze data to formulate plans aimed at neutralizing or reducing the impact of potential threats. Therefore, threat intelligence serves as a proactive measure that equips security teams to diminish the likelihood of serious harm occurring. Organizations can gain significant advantages from threat intelligence, especially when making security infrastructure investments or ensuring compliance with regulations. Beyond aiding in risk assessments, threat intelligence provides crucial insights that facilitate swift and effective responses to incidents.
Different Techniques in Cyber Threat Intelligence
Now that we recognize the importance of threat intelligence, let's delve into the various techniques employed by threat analysts to gather this invaluable information.
Open Source Intelligence
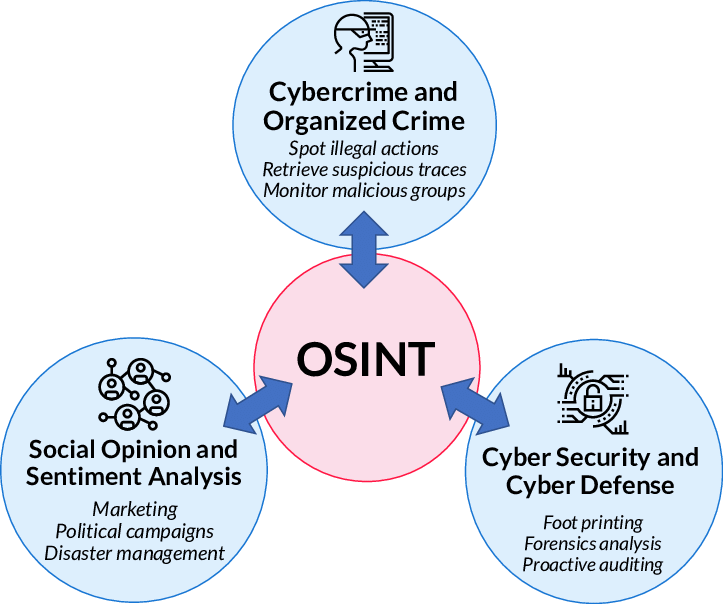
Open Source Intelligence involves extracting data from publicly available resources such as websites, bulletins, and publications. Organizations of all sizes can leverage this timely and cost-effective information. Threat analysts compile data from diverse sources, necessitating a wide range of expertise. The tools designed for this purpose are user-friendly, making them accessible even to novices.
Human Intelligence
Human intelligence involves gathering insights from interpersonal interactions and engagement. This approach can unveil previously hidden insider information through observation or interviews, providing a unique perspective on threats.
Technical Intelligence
As the name suggests, technical intelligence requires specialists to analyze data obtained from technological sources like electronic communications, hardware, and networks. This type of intelligence can relate to malware, intrusions, vulnerabilities, and other digital threats. Such analysis is typically conducted by professionals through network monitoring, log analysis, malware detection, vulnerability scanning, and incident response.
Dark Web Intelligence
To understand dark web intelligence, one must first define the dark web as a segment of the internet that is not indexed and requires special authorization to access. Despite its hidden nature, it can contain valuable threat-related information, including insights into criminal activities, analysis of compromised data, identification of threat actors, and disclosure of recent vulnerabilities.
Best Practices for Cyber Threat Intelligence
Establishing a Threat Intelligence Program
Implementing a robust threat intelligence program is crucial for proactively identifying and assessing threats. Such systems can enable organizations to counteract potential dangers before they escalate into significant issues.
Clear Objectives and Dedicated Resources
For effective risk identification, organizations must prioritize threat intelligence and allocate sufficient resources annually to engage qualified professionals supported by skilled teams. Access to appropriate tools is essential for efficient operations. Organizations should ensure they have the necessary resources and personnel for data gathering and analysis, as resource shortages can hinder effectiveness.
Continuous Monitoring and Collaboration
Given the dynamic nature of threat analysis, companies must maintain constant vigilance over their infrastructure and resources. Adapting to emerging threats and evolving business requirements is essential for effective threat management.
Ongoing Improvement with Timely Reporting
Organizations should be responsive to feedback, whether from internal teams or external sources, to enhance their threat intelligence programs. Timely reporting is critical; delays can lead to escalated issues, making prompt decision-making essential when a potential threat is detected.
Every six months, organizations should evaluate the effectiveness of their tools. If a superior tool is identified, transitioning to it can enhance monitoring and threat intelligence capabilities.
Conclusion
With the growing number of threats, organizations must take this matter seriously to identify potential dangers swiftly. The implementation of threat intelligence programs should not be secondary to infrastructure protection. These programs can significantly reduce the likelihood of new threats emerging, but they require ongoing commitment from organizations.
In this blog post, I outlined several best practices for effective threat intelligence. While additional practices may exist, their specifics can vary between organizations, so it is important to adapt these recommendations to fit your unique context.
This first video covers "Cyber Threat Intel war stories and day-to-day best practices," offering insights into real-world applications and experiences in threat intelligence.
The second video titled "Cyber Threat Intelligence Q&A - Getting started, best practices, mitigating risk, and more!" discusses foundational concepts and strategies for effective threat intelligence.