Navigating Subdomain Takeover Vulnerabilities: A Personal Journey
Written on
Chapter 1: Understanding Subdomain Takeovers
A subdomain takeover is a situation where an attacker gains unauthorized control over a subdomain of a target domain. This typically occurs when a subdomain has a Canonical Name (CNAME) set in the Domain Name System (DNS), but lacks a host delivering content. This can arise from either an unpublished virtual host or the removal of an existing one. By providing their own virtual host, an attacker can then host content on that subdomain.
As I embarked on my bug bounty journey, I initially steered clear of subdomain takeovers. You might wonder why. To be honest, achieving success in this area often relies on a bit of luck. This isn't the typical subdomain takeover story you might find online; it’s more about fortunate circumstances aligning with the right conditions that led to a successful vulnerability report.
Section 1.1: The Story Behind the Report
After a month of waiting, I received a response regarding my report of a subdomain takeover on thesenuts.org (a fictional name). This site was linked to GitHub. While I don't recall the exact details now, I'll do my best to recount the events surrounding this report.

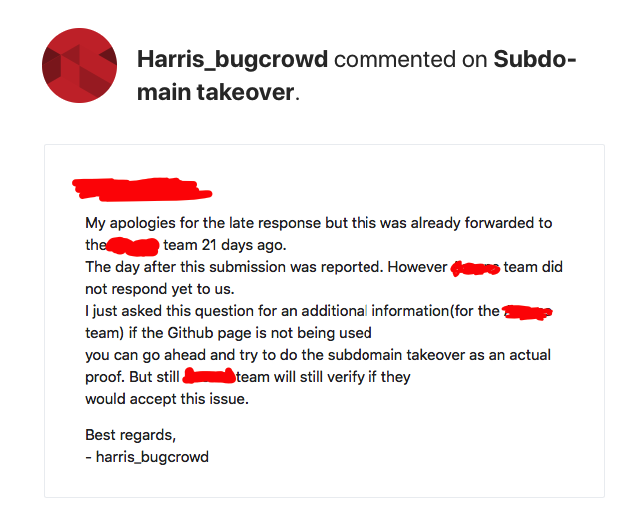
To officially report a subdomain takeover, you need to gain control of that subdomain. After numerous attempts and feeling exhausted at 4 AM, I submitted my report without having taken control. This decision came back to haunt me. After forwarding my report to the Thesenuts team, the triager unexpectedly asked me to take over the subdomain.
Subsection 1.1.1: The How-To Guide
To take control of the subdomain, I would need to create a GitHub account and link it to thesenuts.io. However, this proved to be impossible.
Section 1.2: Recognizing the Opportunity
When I encountered an error page, I suspected it could indicate a potential account takeover. It was clear that thesenuts.io was not actively used by thesenuts.org. Deleting DNS records is a common practice for organizations that discontinue services, serving as a protective measure against such attacks. Unfortunately, in this case, that precaution had not been taken.
Chapter 2: The Waiting Game
Fifteen days passed since the triager's request for me to take over the subdomain, which I had declined for understandable reasons. After many attempts and some social engineering, I decided to wait for the company's response. Eventually, a representative from Thesenuts.org reached out to me, explaining that they had been delayed due to the pandemic.
The Outcome of My Efforts
The response I received was thorough and informative. The representative clarified the issues surrounding Thesenuts.github.io and why I couldn’t claim it.
The Reward: A Pleasant Surprise
This is the most rewarding aspect of the entire experience. The team was generous enough to offer compensation for my efforts.
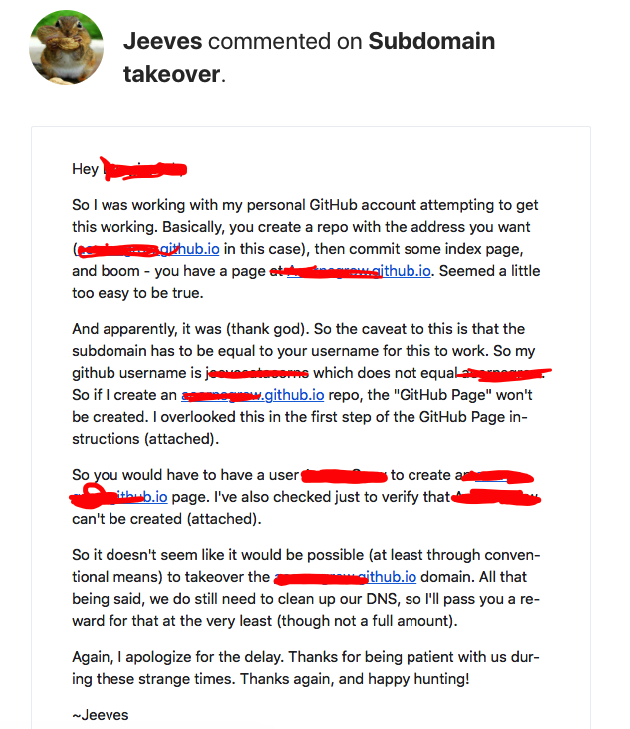
Despite the account not being vulnerable to a subdomain takeover, they still recognized the need for DNS cleanup.
Timeline of Events
- Mar 29, 2020 4:30 AM — Issue reported
- Mar 30, 2020 — Report opened by triager and sent to Thesenuts.org
- April 20, 2020 — Triager confirmed the report was forwarded to the Thesenuts.org team
- May 6, 2020 — Response received from Thesenuts.org, and payment processed on the same day
Was the wait worth it? Absolutely.
Conclusion: Embracing the Unexpected
This experience was more about luck than a straightforward vulnerability. Although I chose to ignore the triager's request, I was fortunate that my report wasn't dismissed immediately. Instead, I waited for the company’s decision, which ultimately led to a positive outcome.
Don't let uncertainty hold you back. When I received the initial email urging me to exploit the vulnerability, I recognized the challenge ahead. However, I remained optimistic and chose to allow Thesenuts.org the time to respond. In many cases, a company's actions can differ significantly from a triager's advice. If you're fortunate enough to have your report escalated to the company, your chances of receiving a reward increase dramatically.
Never give up!
This video explores the nuances of subdomain takeover vulnerabilities and how to identify them effectively.
This video demonstrates a subdomain takeover process, showcasing techniques for stealing websites.